Every year, the Verizon Data Breach Investigation Report (DBIR) delivers critical insights into the state of information security. This year was no different, highlighting areas of concern and opportunities to strengthen cybersecurity measures based on recent trends. Here are six takeaways we found throughout the Verizon DBIR, reminding us that merchants must always remain vigilant about their cybersecurity efforts.
1. Credential Theft Remains a Primary Threat
Stolen credentials made up 22% of breaches. What was the main way that malicious actors were able to access these credentials? Infostealer (information stealer) malware on devices that contained both personal and business credentials. This emphasizes the fact that even corporate-issued devices are vulnerable to today’s top threats.
2. Vulnerability Exploitation Continues to Increase as an Initial Access Vector
Exploitation of vulnerabilities as an initial attack increased by 34% over last year’s figures, now accounting for 20% of breaches. Attackers continue to increasingly target devices and VPNs with zero-day exploits, underlining the need for proactive measures such as zero-trust architecture rather than solely relying on responsive patches.
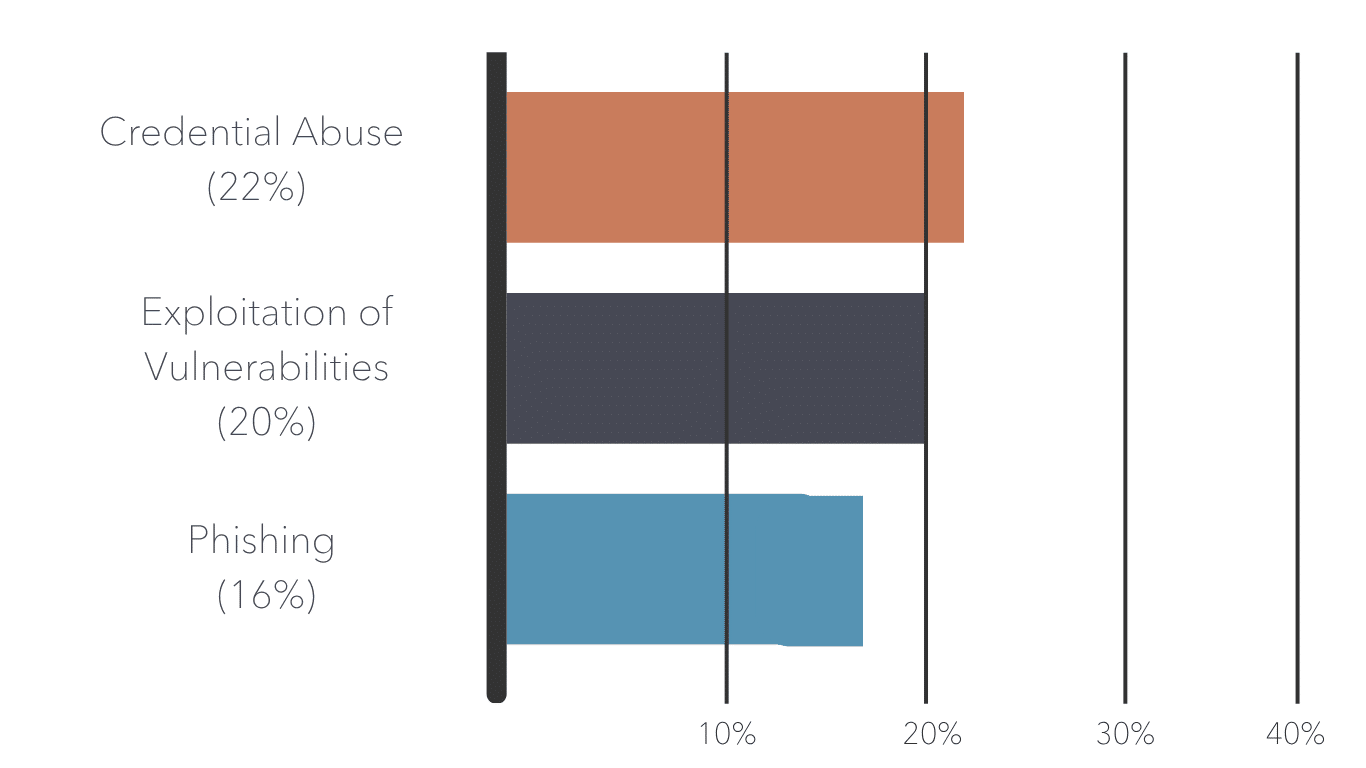
3. Human Error Continues to Be a Significant Factor
With users often clicking on malicious phishing links and unsuspectingly providing data directly to hackers, human error contributed to about 60% of breaches. The need for enhanced user education and awareness is imperative.
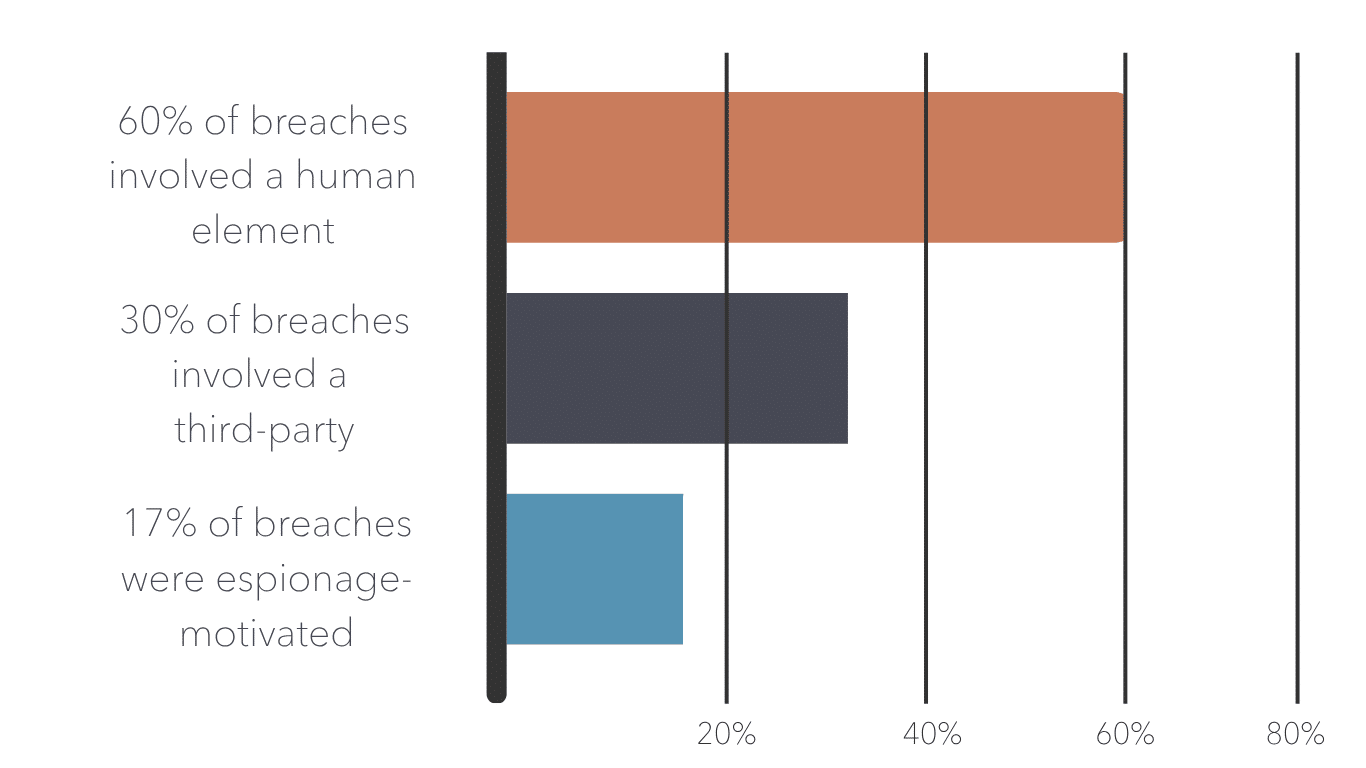
4. Rise in Ransomware and Extortion Attacks
With a 37% increase from last year, ransomware was present in 44% of breaches. Even though the median ransom payment decreased ($115,000), the need for comprehensive backup and recovery strategies is still extremely prevalent.
5. Escalation of Third-Party Breaches
Third-party breaches doubled to 30%, emphasizing the risks associated with supply chain and partner ecosystems. Monitoring the security posture of your third-party vendors is a must.
6. Emerging Threats from Generative AI
The Verizon DBIR notes an increase in the use of generative AI by threat actors. Additionally, 15% of employees were found to be accessing generative AI systems on corporate devices. This was found to be often outside of corporate policy, thus raising concerns about data leakage. While we’ve reached a point of needing to accept the presence of AI in our online activities, companies must make a specific effort to evaluate and create strategies to mitigate the new security concerns that these tools will introduce.
One Positive Trend: A Reduction in Payment-Related Breaches
For the third year in a row, we saw a decline in the number of successful breaches that involved payment data. Card tokenization and EMV/chip card terminals are successfully limiting the number of places where card data is stored – in turn reducing the amount of data that hackers are able to steal if they do access a merchant’s network.
At Curbstone, we’re here to support you through your ongoing data protection efforts. Whether you’re a small business that is just getting started or a larger business that has been around for years, cybersecurity should be a critical focus for your team. If you need help taking the complexity out of your credit card protection efforts, contact us and let us help you get started.

